As I had “fun” at work with some Issues due to fragmented packets to reach a VM in Azure, and except for some posts about the problem12, there were not too many details, and nothing related to the Azure VPN-Gateway, which also exhibits the fragmentation problem, even if it doesn’t go through the public internet and shouldn’t hit any Loadbalancer or other stateful device.
IPSec VPN-Gateway
The first issue was to get fragmented SNMP-Packets delivered to a VM within Azure. As already described that doesn’t work over the public internet. What was not explicitly mentioned, is that it is also true for the IPSec VPN-Gateway, which also sends the traffic through the Software Loadbalancer which is causing the problem. Just as a “funny” note, if you are using OpenVPN instead of IPSec on the same Gateway there are no issues with fragmented packets from Clients… These are some Screenshots from Wireshark from the VPN-Router and the Azure VM. Shown are the SNMP-Request, the answer, and the TTL-Exceeded due to reassembly time exceeded.
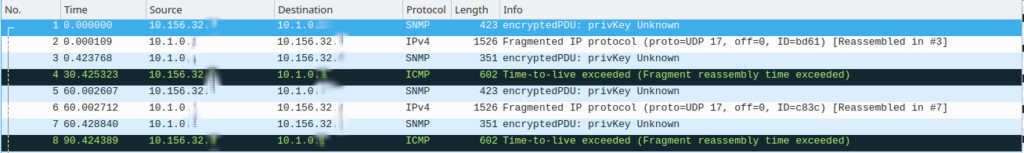
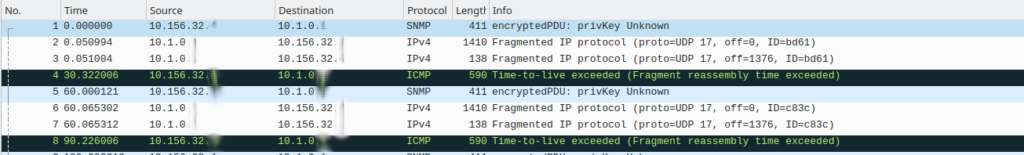
As can be seen on the VM, it is possible to receive fragments, but only up to an original IP-Packet size of 1500 bytes, as the last fragment with the payload above 1500 is dropped. The fragment caused by the IPSec-Tunneloverhead isn’t dropped. So not every Fragment is dropped. This behavior was also confirmed by Microsoft Support, this is a limitation due to the Software Loadbalancer. Alternatives are using a virtual Firewall which is terminating the IPSec or using an Express Route.
Azure networking and out-of-order fragments
If you successfully circumvent the first challenge with a virtual Firewall, there is still a possible Problem, that can cause issues. Fragments that are not arriving in the correct order are also dropped3. This can be disabled on request by support, but you should point to the Microsoft internal link within the GitHub Issue in the footnotes. If you see something like in the next capture (Fragment order is 1, 3, 2 instead of 1, 2, 3), you have to contact support, or if you’re lazy can try to activate forced reassembly of packets in the Firewall.
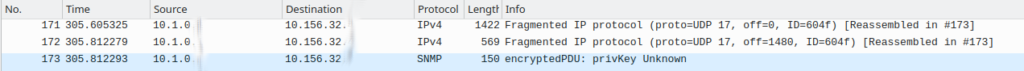
- https://social.msdn.microsoft.com/Forums/vstudio/en-US/310f791b-f19e-44a8-b69d-135bbde6e629/ip-fragmented-udp-packets-of-any-length-are-getting-dropped-by-azure?forum=WAVirtualMachinesVirtualNetwork
- https://stackoverflow.com/questions/56163872/udp-packets-from-a-field-device-will-not-through-azure-infrastructure-to-my-serv
- https://github.com/MicrosoftDocs/azure-docs/issues/69477
